
Recover Hacked Crypto from Trezor Hardwallet
Trezor has always been seen as the gold standard for crypto security — open-source firmware, reproducible builds, and transparent design. For many investors, it’s the final line of defense between hackers and hard-earned digital assets.
But since early 2024, Trezor users have reported an alarming new wave of targeted phishing emails, fake firmware updates, and wallet drains linked to a third-party data breach.
What was once considered a fortress for self-custody became the target of a sophisticated attack campaign — one that leveraged compromised customer data to trick even the most cautious users.
The Red Flag: Phishing Attacks on Unique Email Addresses
One of the earliest signs something was wrong came from Trezor users who are known for their privacy discipline. Many create unique, single-use email addresses for every crypto-related service — so when phishing emails started showing up in inboxes used only for Trezor, it raised suspicion.
Messages titled “Trezor Security Alert” or “Firmware Vulnerability Notice” began appearing, urging users to “verify their seed phrase” or “update firmware immediately.”
These were not random scams. They were surgically targeted phishing campaigns using the same branding, language, and tone as legitimate Trezor communications — a direct result of a data leak that linked email addresses to verified hardware wallet owners.
Bitreclaim’s Forensic Investigation
When affected users approached Bitreclaim, our smart contract engineers and blockchain forensic analysts launched a detailed audit of multiple cases in August and September 2025.
By correlating timestamps, phishing templates, and on-chain activity, Bitreclaim traced over $2.7 million in stolen BTC, ETH, and USDT across several compromised Trezor wallets.
Using Burpsploit and proprietary blockchain graphing tools, our team tracked funds through multi-hop wallets, cross-chain bridges, and mixing services — ultimately identifying common wallets associated with the phishing campaigns.
The 2024 Vendor Breach: The Real Cause Behind the Attacks
What Bitreclaim’s Smart Contract Engineers Discovered
After months of forensic review, Bitreclaim confirmed that this wasn’t a random coincidence. It matched what had been widely reported in 2024:
Trezor had one of their third-party support ticketing vendors breached, exposing customers’ personal data — including email addresses, phone numbers, shipping addresses, and metadata linked to wallet ownership.
The leaked dataset was later sold on dark web markets, giving cybercriminals access to a verified list of hardware wallet owners. These attackers then launched targeted phishing campaigns, impersonating Trezor to deliver malicious firmware links.
Even if only the email address was leaked, many attackers could cross-reference that data with information from other public breaches (like Adobe, LinkedIn, or Dropbox) to build complete victim profiles.
The result? A precision attack surface against known crypto holders — engineered to bypass randomness and focus only on profitable targets.
The Phishing Trap: Fake Firmware Update Email
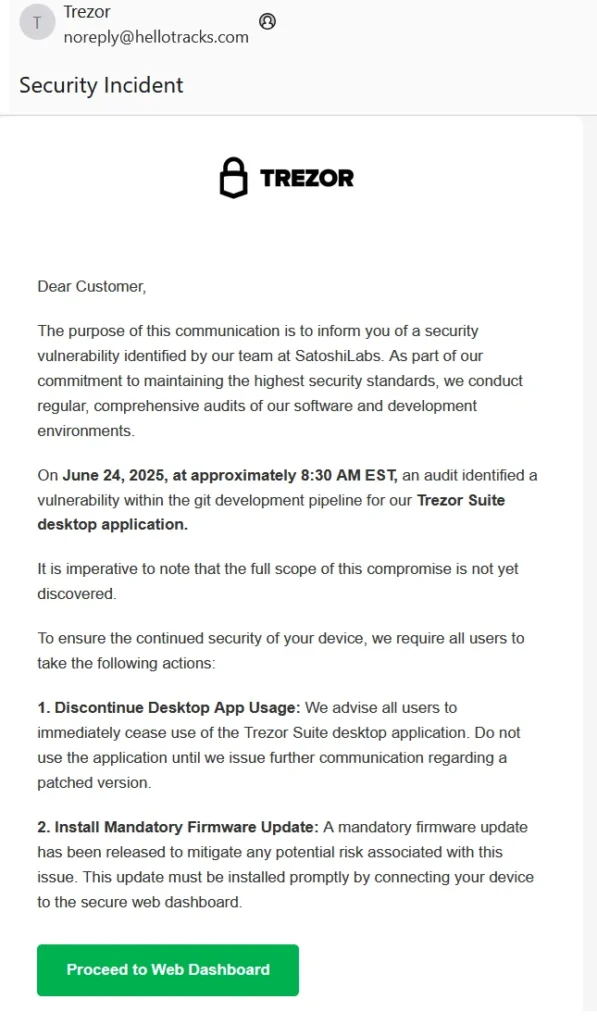
How the Attack Worked
Here’s an excerpt from one of the fake “Critical Vulnerability” emails analyzed by Bitreclaim:
Subject: “Trezor Logo Critical Vulnerability Notice”
Body: “Dear Customer, we discovered a zero-day exploit in Trezor Suite allowing Remote Code Execution (RCE). Please update your firmware immediately.”
[Proceed to Web Dashboard]
“Your security is our highest priority.”
The malicious link led users to a spoofed Trezor dashboard that looked legitimate — right down to the logo and SSL certificate — but it installed compromised firmware or prompted users to enter their seed phrases.
Victims who interacted with these sites saw their wallets drained within minutes, often without realizing it until they reconnected later.
How Bitreclaim Recovered Stolen Funds
The Forensic Recovery Process
- Transaction Hash Analysis
Mapping outbound transactions from the compromised Trezor wallets to identify receiving wallets and contract signatures. - Smart Contract Audit
Examining any exploited contracts or on-chain triggers used by the attacker, verifying if the loss was tied to phishing payloads or fake firmware. - Blockchain Graphing & Mixer Correlation
Using AI-assisted blockchain graphing to follow funds across layers — including Tornado Cash clones, cross-chain swaps, and stealth address generators. - Exchange Escalation & Asset Locking
Coordinating with regulated exchanges and forensic recovery partners to trace and freeze stolen funds before liquidation.
Through this process, Bitreclaim successfully recovered portions of lost BTC and ETH for affected clients, with higher recovery rates for cases opened within 48 hours of compromise.
Lessons from the Trezor Hack
The breach demonstrated that security is only as strong as the weakest link — and that link can sometimes be a vendor, not the product itself.
Trezor’s hardware and firmware remain secure in principle, but the 2024 support vendor breach created a massive vulnerability at the user-data layer. Attackers didn’t need to crack encryption — they simply masqueraded as Trezor support and let fear do the rest.
Bitreclaim’s forensic cases show that this campaign was coordinated, not random, using leaked metadata to personalize attacks. Many victims received phishing attempts referencing real order numbers or shipping dates — a clear indicator that the data came from inside a connected system.
Protecting Yourself Against Hardware Wallet Phishing
Practical Security Tips for Trezor Users
- Never click links in “security” emails. Always navigate manually to the official Trezor website.
- Verify domains carefully. Official communications come only from
@trezor.ioor@satoshilabs.com. - Enable the hidden passphrase feature on your Trezor for additional protection.
- Keep your seed phrase offline. Never type it into any website or email form.
- Separate your storage. Keep long-term holdings in cold storage disconnected from any online activity.
- Report incidents quickly. Time is critical for recovery — forensic traces degrade as funds move.
The Bottom Line: You Can Recover Stolen Crypto
Bitreclaim’s investigations proved that, while attackers are evolving, so are the tools available to fight back. By combining smart contract analytics, AI-based tracing, and forensic recovery workflows, our team has helped victims trace, lock, and reclaim stolen digital assets from complex thefts — including those linked to the 2024 Trezor vendor breach.
Need Help Recovering from a Trezor Hack?
If your Trezor wallet was compromised, or you’ve received suspicious “update” emails that led to fund loss, open a forensic case with Bitreclaim immediately.
Our engineers will analyze your wallet, trace the flow of stolen crypto, and pursue recovery through blockchain, exchange, and smart contract evidence.
Visit bitreclaim.com to begin your case and consult with our blockchain recovery experts today.
recover hacked crypto from trezor hardwallet
recover hacked crypto from trezor hardwallet





4 Responses
never thought I would recover a cent after falling for an online investment scam that stole over $114,000 in Bitcoin. The scammers disappeared, and I was devastated. AfteIr researching crypto scam recovery, I found Bitreclaim and reached out. Their team of specialists quickly requested all my evidence, including wallet addresses, transaction hashes, and screenshots, so they could launch a smart contract audit and detailed crypto fraud investigation. Their crypto recovery service used advanced blockchain forensics to trace my stolen cryptocurrency. Within weeks, I saw results. If you want to recover stolen cryptocurrency or recover lost bitcoin, my advice is to immediately open a case with the 24/7 customer support on Bitreclaim.com and collate all wallet addresses and transaction hashes generated for faster replies
When my crypto was stolen through a fake mining pool dApp pretending to be linked to Coinbase, I turned to Bitreclaim. Their smart contract audit team dissected every transaction and got a portion of my BTC back. Victims, send all wallet addresses, full transaction history, and any evidence to bitreclaim.com —they act fast.
The Pig-Butchering Romance Scam (Singapore, 220k USDT)
I met someone on a dating app who introduced me to “crypto trading.” Within weeks, I had invested S$220,000 in USDT. Every time I tried to withdraw, more “fees” appeared. It was all a scam.
BitReclaim.com treated me with compassion when I felt the most ashamed. Their forensic team traced my USDT across multiple leveraged accounts and exchanges. Ten days later, I had 185,000 USDT back.
If you’ve fallen into a pig-butchering scheme, please don’t stay silent. Contact BitReclaim.
How BitReclaim.com Recovered Stolen Cryptocurrency
In countless cases, BitReclaim has been instrumental in recovering lost, stolen, or scammed cryptocurrency. Whether the theft occurred due to a front-end attack, phishing, or a fake investment platform, their expert team has managed to trace transactions across multiple wallets and recover funds for victims.