How to Avoid Crypto Phishing Scams and What to Do If Your Wallet Is Compromised
How to Avoid Crypto Phishing Scams and What to Do If Your Wallet Is Compromised
Crypto phishing scams have become one of the fastest-growing causes of digital asset loss worldwide. Unlike old-school hacks that relied on brute force, modern crypto phishing attacks are quiet, deceptive, and often look completely legitimate. Many victims don’t even realise anything is wrong until their wallet balance drops to zero.
At Bitreclaim, a blockchain forensic and smart contract audit firm, a large percentage of recovery cases begin with phishing especially involving Ledger wallets, browser extensions, fake updates, and compromised approvals. This guide explains how these scams work, how to avoid them, and the correct crypto wallet recovery steps if you’ve already been affected.
How Crypto Phishing Scams Actually Work (Not the Simplified Version)
Most people imagine phishing as “someone stole my seed phrase.” In reality, that’s now the least common scenario.
What we see more often includes:
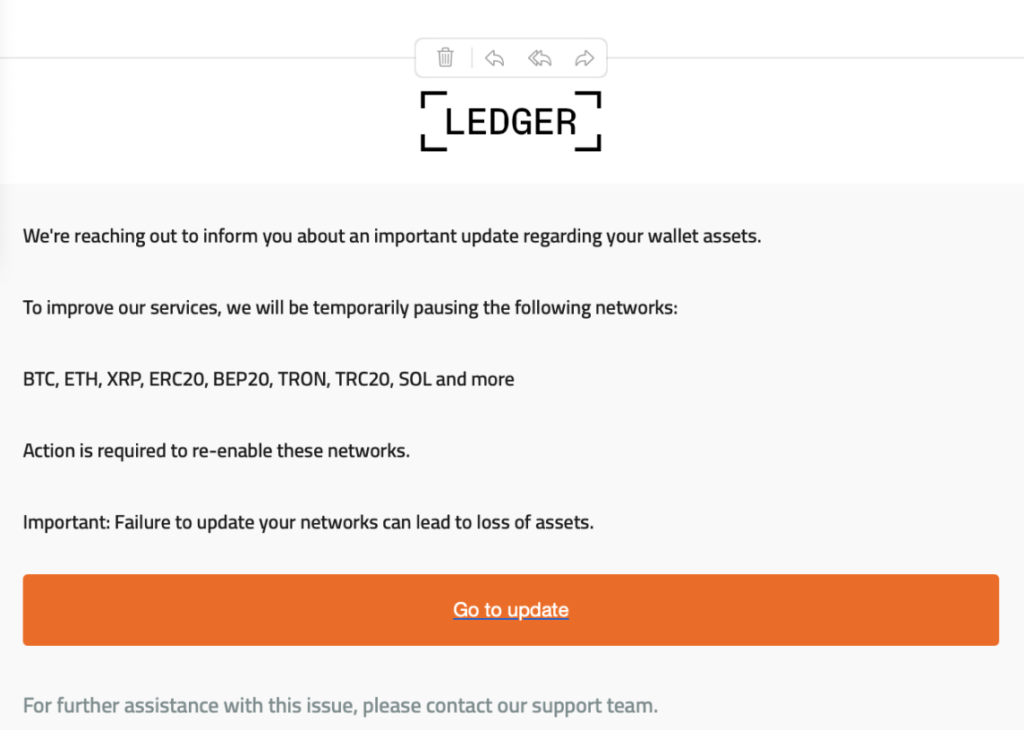
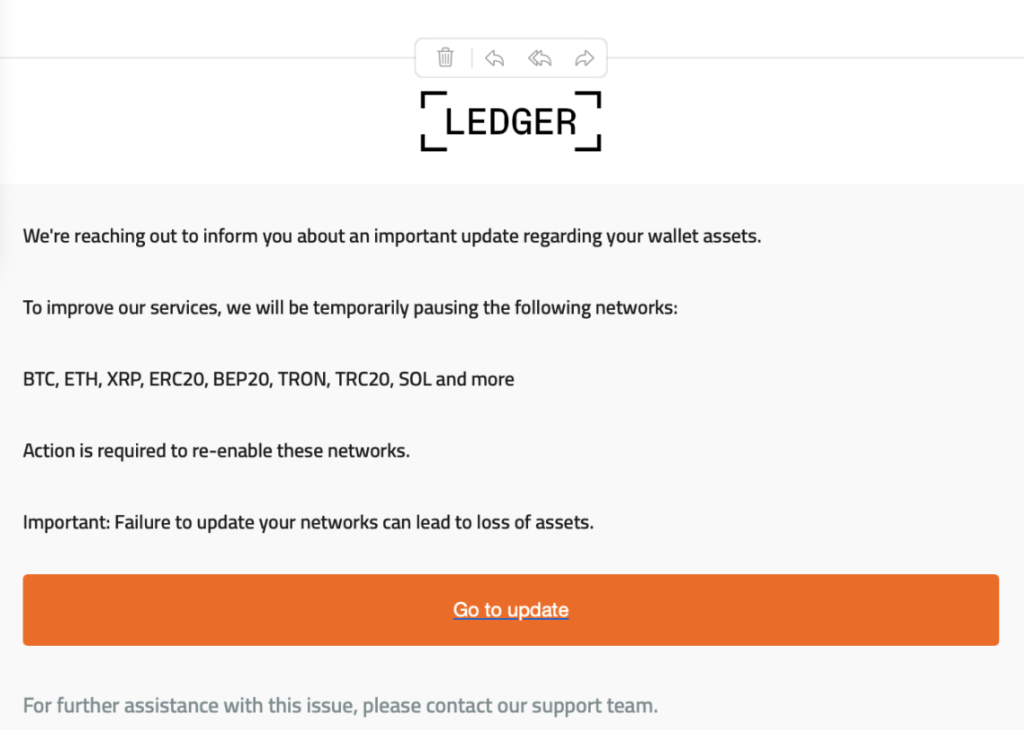
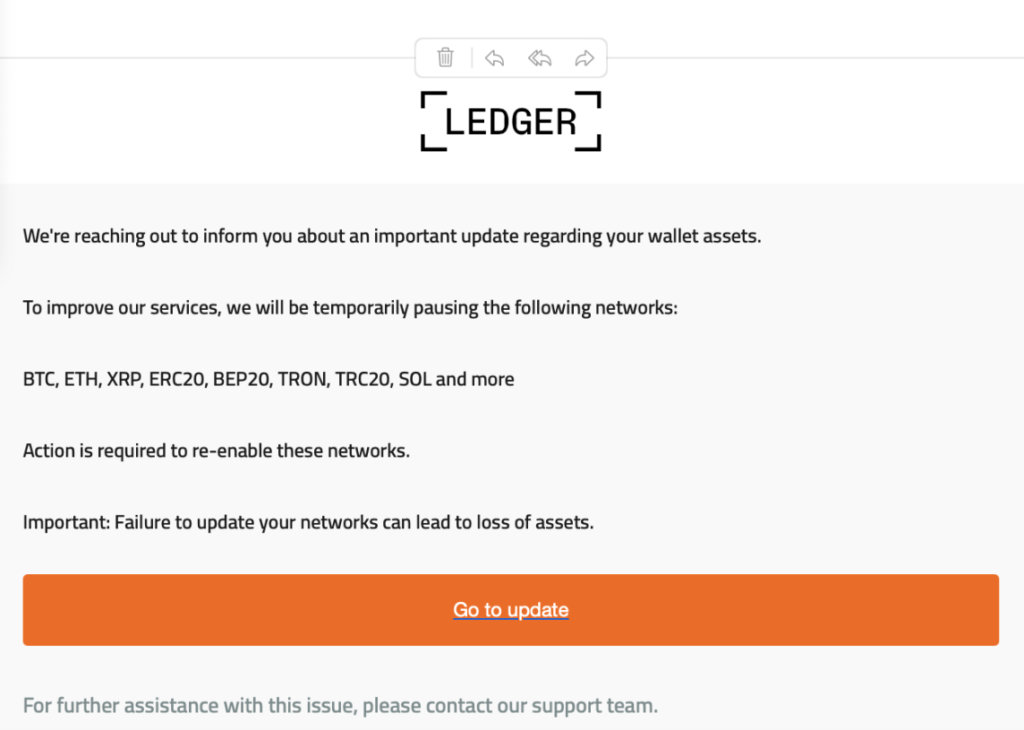
- Fake Ledger or wallet “security update” emails
- Lookalike wallet websites and cloned apps
- Malicious transaction signing masked as verification
- Address poisoning on Ethereum and other EVM chains
- Unlimited token approvals hidden in normal-looking prompts
In many cases, the wallet itself passes all safety checks. The device is genuine. The seed phrase was never shared. Yet the funds are still drained.
That’s because phishing today targets human trust and transaction logic, not just passwords.
How to Avoid Crypto Phishing Scams (What Actually Works)
1. Never trust links in crypto-related emails
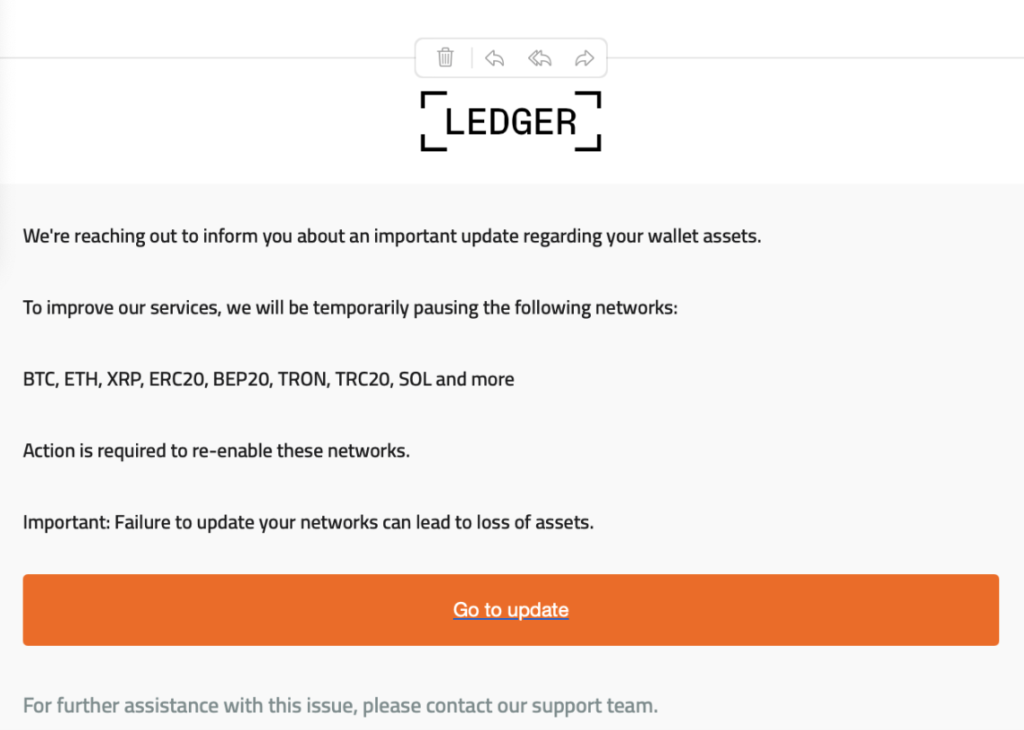
No legitimate wallet provider will ever send you:
- Urgent “update now” emails
- Security alerts asking you to click links
- Requests to “re-verify” your wallet
If an email claims to be from Ledger, MetaMask, Coinbase, or any wallet provider, do not click anything. Go directly to the official site by typing it yourself.
2. Treat every transaction signature as a contract
When you sign a transaction, you are not “logging in.”
You are authorising code.
Many phishing scams rely on users approving:
- Unlimited ERC-20 spending
- Malicious smart contract permissions
- Hidden delegate calls
If you don’t fully understand what a transaction does, do not sign it.
3. Watch for address poisoning
Address poisoning is when scammers send tiny amounts of crypto to your wallet so a fake address appears in your transaction history. Victims then copy the wrong address when sending funds later.
Always:
- Double-check the first and last characters of addresses
- Avoid copying addresses from transaction history
- Use address books when possible
This method has been responsible for six-figure USDT losses in multiple Bitreclaim cases.
4. Keep wallets segregated
Never store all assets in one wallet.
A safer structure:
- Cold wallet for long-term holdings
- Hot wallet for daily activity
- Separate wallet for DeFi and testing
This limits damage if one wallet is compromised.
Crypto Wallet Recovery Steps (If You’ve Already Been Phished)
If you suspect phishing or unauthorised transactions, do not panic and do not move funds blindly. Poor reactions often make recovery impossible.
Step 1: Stop interacting with the compromised wallet
Do not:
- Revoke approvals randomly
- Connect to more dApps
- Try “one last transaction”
Every interaction leaves a trace and may alert the attacker.
Step 2: Secure remaining assets immediately
If any funds remain:
- Move them to a brand-new wallet created on a clean device
- Do not reuse seed phrases
- Do not import compromised wallets into new software
Step 3: Preserve evidence
This step is critical and often overlooked.
You should gather:
- Wallet addresses involved
- Transaction hashes (TXIDs)
- Network details (ETH, BTC, TRON, etc.)
- Screenshots of emails, websites, or fake apps
- Dates and timestamps
This information is what allows blockchain forensic teams to trace funds properly.
Step 4: Open a detailed forensic case
At this stage, recovery is no longer a DIY task.
A professional smart contract audit and blockchain forensic investigation can:
- Identify the exact exploit used
- Trace stolen funds across wallets and chains
- Detect approval abuse and contract interactions
- Flag laundering routes through bridges and exchanges
This is the role Bitreclaim plays in recovery cases.
How Bitreclaim Approaches Crypto Recovery
Bitreclaim is an American blockchain forensic firm working with victims globally, including a high volume of cases from Australia, the UK, Europe, and North America.
Rather than offering false promises, Bitreclaim focuses on:
- Smart contract audits
- Transaction graph analysis
- Wallet clustering
- Cross-chain tracing
- Evidence-grade forensic reporting
In multiple phishing-related cases, Bitreclaim has successfully traced and followed over 7,000 BTC across outsourced wallets using transaction hashes, wallet addresses, and on-chain behaviour analysis.
Can Crypto Lost to Phishing Be Recovered?
The honest answer: sometimes, yes — but only with speed, evidence, and expertise.
Recovery depends on:
- How fast the case is opened
- Whether funds hit identifiable wallets or exchanges
- Whether approvals and contracts can be mapped
- Whether assets are frozen or intercepted mid-laundering
What never works:
- Random “recovery agents” on Telegram
- Promises of guaranteed refunds
- Anyone asking for private keys
Final Advice for Crypto Holders
Phishing scams are no longer amateur attacks. They are organised, technical, and persistent. The best defence is awareness, caution, and understanding that every blockchain interaction matters.
If you believe your wallet has been compromised, the most important step is to document everything and open a proper forensic case rather than guessing or reacting emotionally.
Victims who act early and correctly always have better outcomes.




